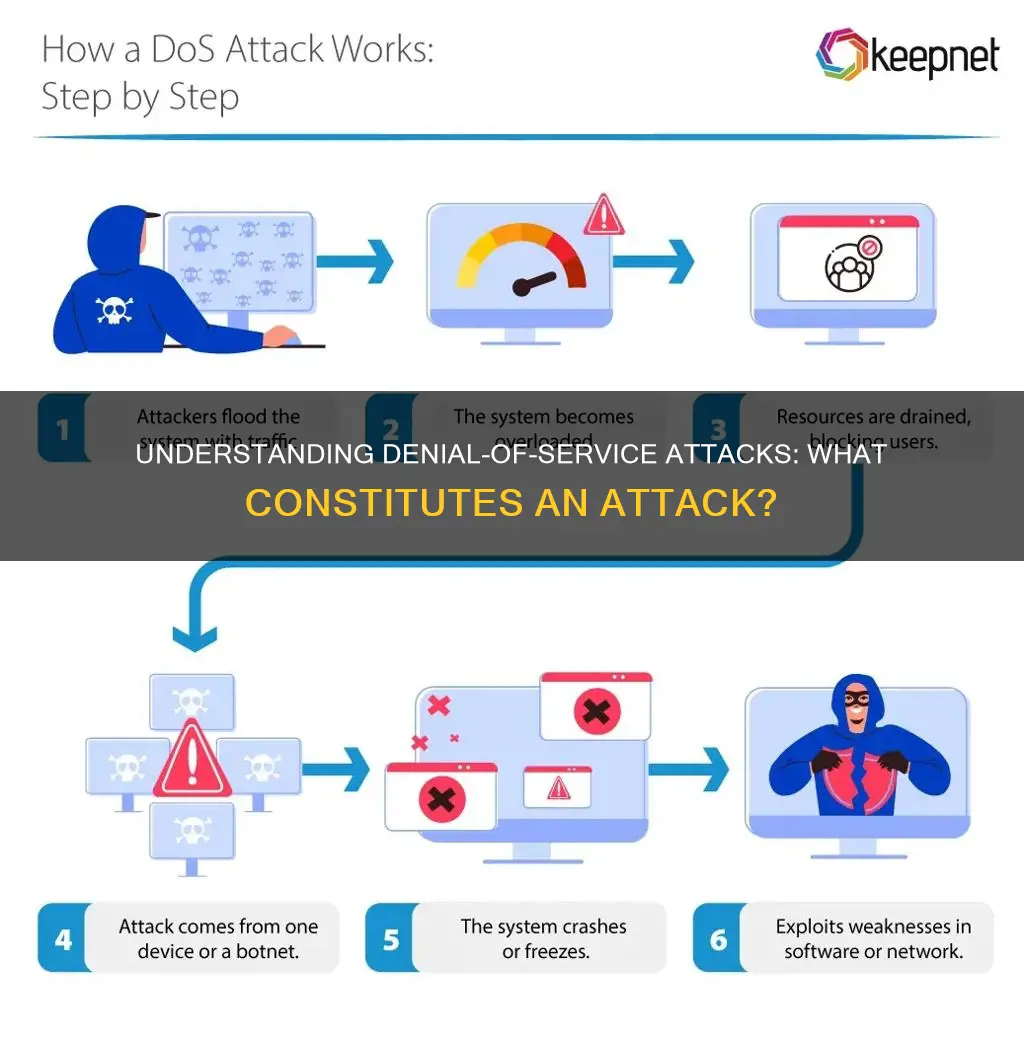
A denial-of-service (DoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming it with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. DoS attacks can be difficult to distinguish from common network activity, but some indications include unusually slow network performance and an inability to access any website. The distinguishing difference between DDoS and DoS is the number of connections utilised in the attack, with DoS attacks utilising a single connection and DDoS attacks utilising many sources of attack traffic.
| Characteristics | Values |
|---|---|
| Type of Attack | Cyber Attack |
| Aims to | Make a machine or network resource unavailable to its intended users |
| Accomplished by | Flooding the targeted machine or resource with superfluous requests |
| Results in | Preventing some or all legitimate requests from being fulfilled |
| Targets | Devices, information systems, or other network resources |
| Affects | Legitimate users |
| Attack Sources | Single computer, multiple computers, botnets |
| Detection | Network traffic monitoring and analysis |
| Symptoms | Unusually slow network performance, inability to access websites |
| Response | Block illegitimate traffic, allow legitimate traffic |
Explore related products

Malicious actors
One common tactic used by malicious actors is the exploitation of multiple compromised computer systems, such as IoT devices, to launch coordinated attacks. This type of attack is known as a distributed denial-of-service (DDoS) attack, where the attacker utilises a network of infected devices without the owners' knowledge. By leveraging a large number of devices, the attacker can generate a massive amount of traffic, making it difficult to differentiate between malicious and legitimate traffic.
DoS attacks can also be carried out using a single computer, where the attacker sends a high volume of requests to the target server, overloading its bandwidth and rendering it unavailable to legitimate users. This type of attack aims to exploit security vulnerabilities in the target's network, software or hardware design.
Additionally, malicious actors may use volumetric floods, protocol abuse, or resource starvation techniques to carry out DoS attacks. They target logging infrastructure, APIs, telemetry channels, or specific features and endpoints to exhaust memory, thread pools, or compute cycles. These attacks can have significant impacts, including system crashes, data theft, and operational disruption, resulting in financial and time losses for organisations and consumers.
To protect against these malicious actors, it is crucial to strengthen the security posture of internet-connected devices, install antivirus software, and implement firewalls to restrict and monitor incoming and outgoing traffic.
Understanding Sales Tax Nexus: What Constitutes It?
You may want to see also

Exploiting operational bottlenecks
A denial-of-service (DoS) attack is designed to shut down a machine or network, making it inaccessible to its intended users. It aims to overwhelm a target by consuming finite resources. The target could be a web server, network device, application endpoint, or cloud-based service.
DoS attacks vary in volume, sophistication, and intent. Some seek disruption, while others act as diversions. Adversaries often deploy DoS to mask intrusion. While defenders focus on restoring service availability, attackers exploit the disruption to move laterally, escalate privileges, or exfiltrate data.
DoS attacks can be performed by exhausting the system resources those services are hosted on or exploiting the system to cause a persistent crash condition. Adversaries can target various layers of the application stack hosted on the system, including the Operating Systems (OS), web servers, DNS servers, databases, and the applications that sit on top of them. Attacking each layer requires different techniques that take advantage of bottlenecks unique to the respective components.
Application layer attacks, for instance, make applications unavailable by exhausting system resources or by making them unusable in a functional way. They place an operational strain on the application server, causing the server to become unavailable, unusable, or non-functional. Slow HTTP attacks, for example, deliver HTTP requests very slowly and fragmented, one at a time. Until the HTTP request is fully delivered, the server keeps resources stalled while waiting for the missing incoming data.
To prevent DoS attacks, it is essential to detect and prevent single points of failure (SPOF). Most DoS attacks assume that a system has SPOFs that will fail due to overwhelmed systems. It is recommended to employ stateless components, use redundant systems, create bulkheads to stop failures from spreading across the infrastructure, and ensure that systems can survive when external services fail.
Electoral Authority: Constitutional Powers and Elections
You may want to see also

Botnets
A botnet is a network of personal devices that have been compromised by cybercriminals without the knowledge of the device owners. Botnets are a common tool used in distributed denial-of-service (DDoS) attacks.
The controller of a botnet is able to direct the activities of these compromised devices through communication channels formed by standards-based network protocols, such as IRC and Hypertext Transfer Protocol (HTTP). Botnets can be used to perform DDoS attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command-and-control (C&C) software.
An example of a botnet is the Mirai botnet, which affected more than 500,000 devices connected to the internet. Unlike other botnets that capture private computers, Mirai gained control over easily accessible IoT devices such as internet-connected cameras and recording devices. These weakly secured devices were then used to make a DDoS attack designed to take down the Sony PlayStation Network's gaming platform by sending an insurmountable number of requests to Dyn’s server.
Another example is HTTPBot, a Windows-based botnet trojan that has been used to primarily target the gaming industry, as well as technology companies and educational institutions in China. HTTPBot launched 200+ targeted DDoS attacks in April 2025 using browser-mimicking tactics to bypass defences.
The Supremacy Clause: Understanding the Constitution's Hierarchy
You may want to see also
Explore related products

Smurf attacks
A Smurf attack is a distributed denial-of-service (DDoS) attack that exploits Internet Protocol (IP) broadcast addresses and spoofed source IP addresses to flood a targeted device or network with bogus traffic. The attack amplifies the amount of traffic generated, with the goal of overwhelming the target’s network or device.
The attacker’s initiating ping is multiplied by all the hosts responding, creating an amplification effect that generates floods of traffic directed at the target’s network or device. This is known as the amplification factor, which refers to how much traffic is generated compared to the volume of packets sent by the attacker. For example, an amplification factor of 20-70X means that for a network with 20-70 hosts, each ICMP echo reply packet sent to the victim multiplies the traffic by that factor.
There are several key measures that can be taken to defend against Smurf DDoS attacks, including disabling directed broadcasts, filtering ICMP, implementing firewall rules, and using DDoS mitigation services.
European Thinkers: Framing the Constitution
You may want to see also

Ping floods
A ping flood, also known as an Internet Control Message Protocol (ICMP) flood, is a type of distributed denial-of-service (DDoS) attack. It involves an attacker overwhelming a targeted device or network with a high volume of ICMP echo-request packets or pings. This can cause network congestion and prevent legitimate users from accessing network resources.
In a ping flood attack, multiple compromised systems are used to send a large number of ICMP echo requests to the target. These requests are sent to the broadcast IP address 255.255.255.255, allowing them to reach all connected devices. The target system attempts to respond to each request with an echo reply packet, but due to the high volume of incoming requests, it becomes overwhelmed and unable to handle the traffic. This results in network congestion and legitimate users being denied access to the system.
The Internet Control Message Protocol (ICMP) is a standard internet layer protocol used by network devices to communicate. ICMP echo-request and echo-reply messages are typically used to diagnose the health and connectivity of a device and the connection between the sender and the device. By flooding the target with request packets, the network is forced to respond with an equal number of reply packets, overloading the network connection with bogus traffic.
To defend against ping floods, organisations can implement a multi-layer strategy that includes intelligent traffic filtering, increased capacity, DDoS mitigation services, and emergency response planning. Additionally, disabling the ICMP functionality of the targeted router, computer, or device can help prevent ping flood attacks.
Public Performance Parameters: School Edition
You may want to see also
Frequently asked questions
A denial-of-service (DoS) attack is a malicious attempt to disrupt the normal operations of a web property by overwhelming it with traffic.
A DoS attack works by flooding a targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
A distributed denial-of-service (DDoS) attack is a type of DoS attack that comes from many distributed sources, such as a botnet.
Symptoms of a DoS or DDoS attack include unusually slow network performance and an inability to access any website. The best way to detect and identify an attack is via network traffic monitoring and analysis.
If you suspect a DoS or DDoS attack, contact your network administrator and appropriate technical professionals for assistance.