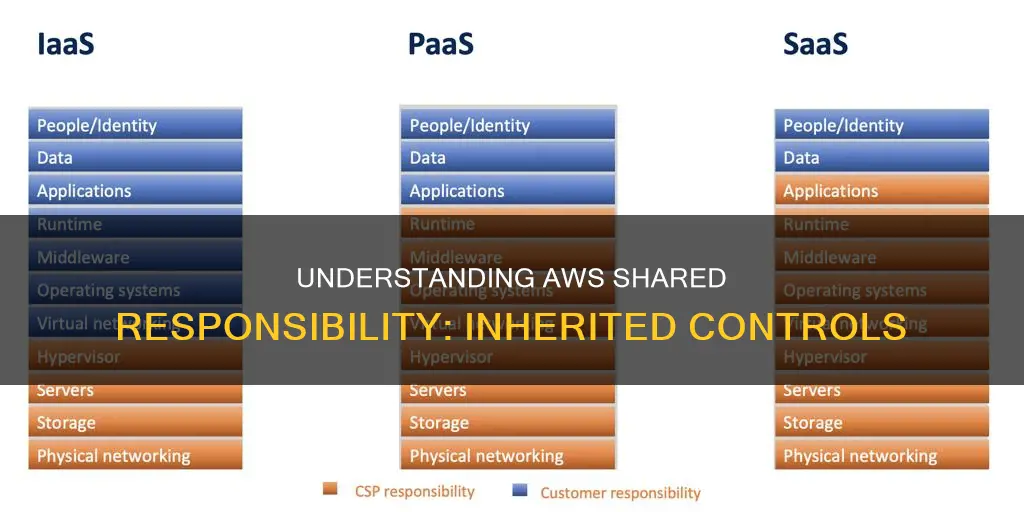
The AWS shared responsibility model outlines the responsibilities of both AWS and its customers. This model extends to IT controls, with both parties managing, operating, and verifying them. Inherited controls refer to the security and environmental controls that customers fully inherit from AWS. These include the physical and environmental security controls used by Amazon, such as the security of the cloud infrastructure, host operating system, and data centres. Customers are responsible for the security within the cloud, including the guest operating system, application software, and the configuration of the AWS security group firewall. The shared responsibility model provides flexibility and control, allowing customers to focus on deploying solutions that meet their specific requirements.
| Characteristics | Values |
|---|---|
| Inherited Controls | Physical and environmental controls of the data centres and their related assets |
| Physical security of the facilities in which the service operates | |
| Security for its infrastructure | |
| Management of the host operating system | |
| Management of the virtualization layer | |
| Maintenance of physical servers | |
| Applying OS patches | |
| Installing firmware updates | |
| Implementing physical security | |
| Shared Controls | Patch Management |
| Configuration Management | |
| Customer-Specific Controls | Service and Communications Protection |
| Zone Security | |
| Awareness and Training |
Explore related products
What You'll Learn

Physical and environmental security controls
The AWS shared responsibility model divides security and compliance responsibilities between AWS and the customer. In terms of physical and environmental security controls, AWS manages the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates. This includes the physical infrastructure deployed in the AWS environment, such as the cloud infrastructure, network, data storage, system resources, data centres, reliability, and supporting hardware and software.
AWS is responsible for configuring and managing the security of the cloud, including the physical security of the facilities in which the service operates. This means that AWS ensures the physical protection of the buildings and infrastructure that house the customer's data and applications.
Customers, on the other hand, assume responsibility for the guest operating system, including updates and security patches, as well as any application software or utilities installed on instances. Customers are also responsible for managing their data, including encryption options, classifying their assets, and using IAM tools to apply the appropriate permissions.
The shared responsibility model provides flexibility and customer control, allowing customers to deploy solutions that meet their specific needs and requirements. Customers can also take advantage of AWS control and compliance documentation to perform their control evaluation and verification procedures.
It is important to note that the specific responsibilities of each party may vary depending on the services used, the integration of those services into the customer's IT environment, and applicable laws and regulations.
John Dewey's Philosophy: Understanding the Core of Experience
You may want to see also

Security and compliance
AWS operates, manages, and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates. This includes the physical infrastructure, network, data storage, system resources, data centres, reliability, and supporting hardware and software.
Customers assume responsibility for the guest operating system, including updates and security patches, other associated application software, and the configuration of the AWS-provided security group firewall. Customers are also responsible for training their employees. The customer's responsibilities vary depending on the services used, the integration of those services into their IT environment, and applicable laws and regulations.
The shared responsibility model also extends to IT controls. The management, operation, and verification of these controls are shared between AWS and its customers. AWS can manage those controls associated with the physical infrastructure deployed in the AWS environment, while customers can use the AWS control and compliance documentation to perform their control evaluation and verification procedures.
Examples of inherited controls include the physical and environmental controls of the data centres and their related assets. AWS is responsible for securing the cloud infrastructure, while the customer is responsible for securing their usage and data within the cloud.
Cabinet Secretaries: Why They Trump White House Staff
You may want to see also

Management of physical infrastructure
The AWS shared responsibility model divides the management of physical infrastructure between AWS and its customers. While AWS is responsible for the security "of the cloud", the customer is responsible for the security "in the cloud".
AWS manages the cloud infrastructure, including the network, data storage, system resources, data centres, physical security, reliability, and supporting hardware and software. This means that AWS takes care of the physical security of the facilities in which the service operates, including the host operating system and virtualization layer. AWS also provides security for its infrastructure, while customers are responsible for the security and configurations of their software components.
On the other hand, customers are responsible for managing their data (including encryption options), classifying their assets, and using IAM tools to apply the appropriate permissions. Customers also assume responsibility for the guest operating system, including updates and security patches, as well as any associated application software. Customers are also responsible for configuring the AWS-provided security group firewall.
The nature of this shared responsibility provides flexibility and customer control, allowing customers to deploy their own specific requirements. Customers can use the AWS control and compliance documentation to perform their control evaluation and verification procedures.
It is important to note that customer responsibilities can vary depending on the specific services used, the integration of those services into their IT environment, and applicable laws and regulations.
McCulloch v Maryland: The Constitutional Clause Explained
You may want to see also
Explore related products

Control evaluation and verification
The AWS Shared Responsibility Model outlines the responsibilities of both AWS and the customer in terms of security and compliance. This model extends to IT controls, with both parties sharing the management, operation, and verification of these controls.
In terms of control evaluation and verification, customers can utilise the AWS control and compliance documentation to perform their control evaluation and verification procedures. This documentation outlines the responsibilities of both parties and provides examples of controls managed by AWS, the customer, or both. By referring to this documentation, customers can understand their specific responsibilities and ensure they are meeting their obligations.
For instance, in the context of patch management, AWS is responsible for patching and fixing flaws within the infrastructure (host OS), while customers are responsible for patching their guest operating systems and applications. Similarly, in configuration management, AWS manages the configuration of its infrastructure devices and servers, while customers are responsible for configuring their guest operating systems, databases, and custom applications.
Additionally, customers should carefully evaluate the AWS services they choose as their responsibilities vary depending on the specific services used, the integration of those services into their IT environment, and applicable laws and regulations. For example, certain services like Amazon EC2 require the customer to perform all necessary security configuration and management tasks, while abstracted services like Amazon S3 and Amazon DynamoDB have different responsibilities.
Third-party audit attestation documents can also be reviewed to determine inherited controls and identify any remaining controls that need to be implemented in the customer's environment. This evaluation process ensures that customers understand their inherited controls and any additional responsibilities they may have.
Constitutional Court Cases: A Historical Overview
You may want to see also

Data security
AWS is responsible for the security "of" the cloud, encompassing the management and control of the underlying infrastructure. This includes the host operating system, virtualization layer, and physical security of the facilities. AWS manages the cloud infrastructure, encompassing data storage, system resources, data centres, and hardware and software. They are responsible for configuring and securing the cloud environment, ensuring data centre security and environmental protection.
Customers, on the other hand, are responsible for security "in" the cloud. This pertains to how they configure and utilise AWS resources and the data they store and manage in the cloud. Customers assume responsibility for the guest operating system, including updates, security patches, and associated application software. They are also responsible for managing their data, including encryption, and classifying their assets. For instance, with Amazon EC2, customers are responsible for security configuration, management, and the configuration of the AWS-provided firewall.
There are also shared controls, where both AWS and the customer have specific responsibilities. These include incident response, awareness and training, and configuration management. For example, in patch management, AWS fixes flaws within the infrastructure, while customers patch their guest operating systems and applications.
Third-party audit attestation documents, such as AWS System and Organisation Controls (SOC) reports, offer insights into the security controls AWS provides and help customers understand inherited controls and any additional controls needed in their environment.
California's Constitution Test: Is It Mandatory for 8th Graders?
You may want to see also
Frequently asked questions
Inherited controls refer to the controls that a customer fully inherits from AWS. These include the physical and environmental security controls used by Amazon, such as the security of the cloud infrastructure, host operating system, and data centres.
Examples of inherited controls include physical and environmental controls of the data centres and their related assets. AWS is responsible for patching and fixing flaws within the infrastructure, while customers are responsible for patching their guest OS and applications.
Security and Compliance is a shared responsibility between AWS and the customer. AWS manages and controls components from the host operating system, virtualization layer, and physical security of facilities, while customers assume responsibility for the guest operating system, associated software, and configuration of the AWS security group firewall.







![Compliance [Blu-ray]](https://m.media-amazon.com/images/I/712fZO6aOlL._AC_UY218_.jpg)












![Law of Governance, Risk Management and Compliance: [Connected Ebook] (Aspen Casebook)](https://m.media-amazon.com/images/I/616gNHR5shL._AC_UY218_.jpg)




















